A ransomware is a malicious program that encrypts all of document, picture and movie files in a computer. And to be able to decrypt them, the user must pay the malware author for some amount of money.
CryptoLocker
This ransomware, once executed, will search for document files that it targets and encrypt them using an RSA algorithm. And the user may pay USD300 to the malware author to recover the encrypted documents. It gives the user options how to pay the ransom (i.e MoneyPak and Bitcoin). If the user chose not to pay, his/her only practical option is to restore from backup.
Physical File Analysis
The sample that I've come across has a green circular icon with a cross inside it and with the following file properties.
I used the combination of OllyDbg and IDAPro in reversing this malware. The reason being is OllyDBg doesn't have compiler symbols which IDAPro is rich of. OllyDbg 2.0 doesn't resolve the WinMain of this sample but IDAPro is able to do so. But I used OllyDbg throughout the debugging as I am comfortable with its 'look and feel'.
This malware is literally self-modifying as it has an encrypted PE file embedded on itself. The decrypted embedded PE Image will overwrite the original file. OllyDbg is able to detect it:
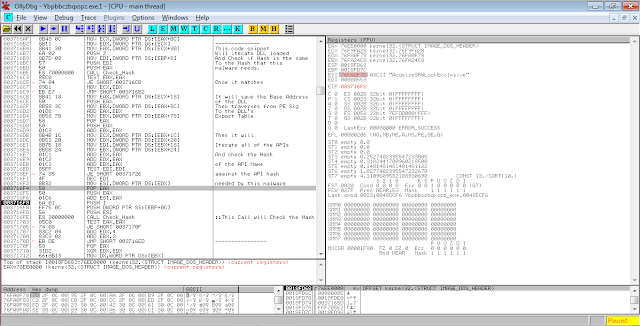
On the first/original binary, the malware APIs are found in hashes and their matching addresses are traversed to their corresponding DLL. On this case, it only uses kernel32.dll to decrypt itself. This technique is usually seen in packers, encryptors and malwares nowadays to make the life of a malware reverser a little bit harder:
0x000D4E88 - kernel32.dll
0x003560DA - LoadLibraryExA
0x000E3142h - VirtualAlloc
0x0038D13C - VirtualProtect
0x00348BFA - GetProcAddress
0x000068AE - FlsFree
Above are the API needed to map the embedded encrypted PE image in the memory. Once mapped, it will then do its decryption routine to reveal the embedded PE Image. This new PE Image will overwritten to the original binary and pass the control to it. I have dumped this new PE Image using Procdump and found out that this new file has an icon of a yellow key. Here's the code that does the said routine:
Global\<random_name1>
Local\<random_name2>
This malware sample drops a copy of itself in %APPDATA%\Local\<random_file_name>.exe where random_file_name is generated with the same way as the mutex names.
Once it dropped a copy of itself, it will spawn a process of the newly created copy of itself with the following CommandLine parameter:
%APPDATA%\Local\<random_file_name>.exe -r%PATH_OF_CURRENT_EXECUTION%\<random_file_name>.exe
This command-line will basically remove/delete the file %PATH_OF_CURRENT_EXECUTION%\<random_file_name>.exe
Now, to debug this new child process, you may follow this:
NOTE: Don't Step over yet on the CreateProcess API. Do the following first:
1. Open the newly created file using any binary editor.
2. Go to entry point.
3. Write down the first 2 bytes.
4. change the first 2 bytes to EB FE
5. Save it.
6. Go back to the debugged parent process.
7. Step over to CreateProcess API.
8. Open a new OllyDbg.
9. Attach the new process created to OllyDbg.
10. Go to the Entry Point.
11. modify back the original 2 bytes.
12. Continue debugging the child process.
This newly created process is multi-threaded and will basically do the rest of its malicious deeds. It will create the following registry entry as part of its auto-run mechanism:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
CryptoLocker="%APPDATA%\Local\<random_file_name>.exe
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
*CryptoLocker="%APPDATA%\Local\<random_file_name>.exe
On this malware sample, it will attempt to connect to the following hard-coded domain:
xqmrainncxrwho.net
After which, it will start generating domain names. This malware uses Domain Generation Algorithm(DGA). The algorithm is based from current System Date (year, month and day) and some hard-coded constants. It will generate a 14 character long domain name and appends any of the following Top Level Domain(TLD):
.net
.biz
.ru
.org
.co.uk
.info
.com
Once generated it will send the following HTTP Request:
POST /home/ HTTP/1.1
Accept: */*
Host: <random_generated_domain>
Connection: Close
If the server responded OK, it will create a BMP image file on the desktop with a randomly generated name. This image file contains the URL where you can download a copy of CryptoLocker:
And then it displays its GUI that contains the ransom message. The user needs to pay USD300 to recover the encrypted documents. The payment methods that it accept are:
MoneyPak
Bitcoin
This malware encrypts files using RSA algorithm. It encrypts all files that it finds which has the following extension names:
*.odt *.ods *.odp
*.odm *.odc *.odb
*.doc *.docx *.docm
*.wps *.xls *.xlsx
*.xlsm *.xlsb *.xlk
*.ppt *.pptx *.pptm
*.mdb *.accdb *.pst
*.dwg *.dxf *.dxg
*.wpd *.rtf *.wb2
*.pdf *.mdf *.dbf
*.psd *.pdd *.eps
*.ai *.indd *.cdr
*.dng *.3fr *.arw
*.srf *.sr2 *.bay
*.crw *.cr2 *.dcr
*.kdc *.erf *.mef
*.mrw *.nef *.nrw
*.orf *.raf *.raw
*.rwl *.rw2 *.r3d
*.ptx *.pef *.srw
*.x3f


















0 comments:
Post a Comment