This trojan comes as a spam email. Here are sample spam emails:
Like some CryptoLocker samples, this trojan uses a very similar decryption method. It uses VirtualAlloc to allocate memory space where it will decrypt the embedded PE Image, and then calls VirtualProtect so that it can overwrite itself with the newly decrypted PE Image and then passes the control to it.
Here's a visual infection flow of this trojan:
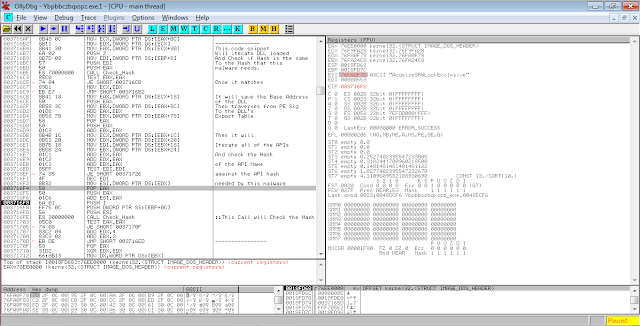
This particular sample that I got to reverse has an interesting anti-debugging technique. It uses RegisterClass and CreateWindowEx as part of its anti-debugging. It will first call RegisterClass to setup the WNDCLASS data structure which contains the address where the next code will go after calling CreateWindowEx.
Once decrypted and pass over the control the new PE Image, it will create a file named "budha.exe" on %TEMP% folder. This file is a copy of the original binary. And then it will execute this newly created file using ShellExecute.
This new process will delete the original binary then it will attempt to download and execute files from compromised sites which are hard-coded in its body. And those files that it downloads are known to be Zbot variants.
Like some CryptoLocker samples, this trojan uses a very similar decryption method. It uses VirtualAlloc to allocate memory space where it will decrypt the embedded PE Image, and then calls VirtualProtect so that it can overwrite itself with the newly decrypted PE Image and then passes the control to it.
Here's a visual infection flow of this trojan:
This particular sample that I got to reverse has an interesting anti-debugging technique. It uses RegisterClass and CreateWindowEx as part of its anti-debugging. It will first call RegisterClass to setup the WNDCLASS data structure which contains the address where the next code will go after calling CreateWindowEx.
Once decrypted and pass over the control the new PE Image, it will create a file named "budha.exe" on %TEMP% folder. This file is a copy of the original binary. And then it will execute this newly created file using ShellExecute.
This new process will delete the original binary then it will attempt to download and execute files from compromised sites which are hard-coded in its body. And those files that it downloads are known to be Zbot variants.