Recently I came across with a macro malware that uses a technique quite new to me. If macro is enabled, macro script does the following:
Upon inspecting the file in Hiew we could see that there is an embedded PE file. But by simply opening the file in Word doesn't mean that the PE file will run in the system, but with the use of macro script that is possible.
- Save the Doc file as RTF file, 300.rtf and 301.rtf
- Open the 300.rtf file with an embedded PE file
- Then execute the PE file
Upon inspecting the file in Hiew we could see that there is an embedded PE file. But by simply opening the file in Word doesn't mean that the PE file will run in the system, but with the use of macro script that is possible.
Existing macro script in files. These macro scripts are password protected.
Extracted Macro script
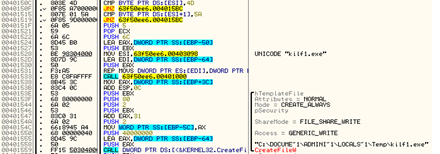
By inspecting 300.rtf we could notice that there is an embedded object.
Using the following instructions macro file were able to open 300.rtf, embedded PE file will be extracted to TEMP folder. Thus, macro script were able to successfully execute the file.
Set sttKaka = CreateObject("Word.Application")
sttKaka.Visible = False
Set docWord = sttKaka.Documents.Open(TCA)
This technique is only feasible using Microsoft Word 2010 and Microsoft Word 2013, with Microsoft 2007 and below it will encounter Privacy Warning.
It is highly adviseable to disable macro to avoid this type of malware from compromising your system.